Proofpoint pitches human-centric cyber defence against AI-generated phishing
More cyber attacks now target the weakest link - humans - to…
Asia-Pacific CISOs face deeper challenges with board leadership: Splunk study
Chief information security officers (CISOs) in Asia-Pacific often have weaker relationships with…
Q&A: Despite early issues, GenAI is set to hugely impact businesses, says Elastic
Data management and trust in GenAI results have been big obstacles for…
Geopolitical rivals meet in Singapore for SICW cybersecurity forum
At SICW, representatives from the United States, China and Russia will be…
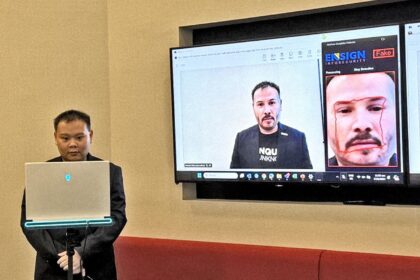
Ensign unveils AI tool that detects deepfakes in real time
The Ensign Aletheia tool detects deepfakes in real time, amid the growing…
Fighting AI with AI: Cybersecurity arms race heats up again
A cybersecurity arms race is on with organisations seeking to use AI…
Unveiling cyber secrets to fortify digital systems at GeekCon 2024
In Singapore, the two-day GeekCon event starting May 25 will be attended…
Southeast Asia tops global ransomware incidents: Trend Micro
Ransomware detections increased alarmingly across Southeast Asia, accounting for over half of…
Five surprising benefits of network visualisation
Network visualisation provides a real-time view of resource utilisation and can be…
Shadow AI poses risk of exposing company data: WalkMe
After combatting shadow IT, organisations now have to cope a new kind…
Why LLM-powered AI tools can be a double-edged sword for businesses
Large language models (LLMs) used to train AI chatbots and other tools…
Driven by cybersecurity, managed services set to grow in Asia-Pacific: Canalys
Managed services are on the uptick in the Asia-Pacific, due to an…
Can a bank like OCBC tell customers what mobile apps they can install?
OCBC needs to improve the way it implements its anti-scam measure and…
Over 400,000 potential Internet-facing vulnerabilities in Singapore’s top firms: Tenable
Over 400,000 Internet vulnerabilities have been found among Singapore's top 25 companies,…
Phishing, ransomware remain key concerns in Singapore, as hackers find success
Phishing and ransomware were the top risks in Singapore in 2022, especially…
Imperva opens network, security ops centre in Singapore to boost Asia-Pacific presence
Imperva has opened a network and security operations centre in Singapore to…
Has adoption of “connected devices” outpaced security?
Our ability to build and deploy intelligent, connected devices has outpaced our…
Q&A: Against new online threats, strengthen defence perimeter and boost cyber hygiene education, says NTT
Businesses must keep strengthening the defence perimeter and educate stakeholders on cyber…
Protect your organisation’s crown jewels: Production data
Using one's production data for software or app development in a staging…
Securing one’s software supply chain in an era of complex, interconnected systems
Securing one's software supply chain is not easy today, but tools that…