With cybercriminals continuing to outsmart enterprises in several high profile security breaches in recent years, it is no longer business as usual for folks in IT security.
Many threats have proven to be capable of breaching firewalls and other defences, so the traditional way of ring-fencing your IT infrastructure is no longer good enough.
What’s needed is a way to suss out both internal and external threats before they happen. Darktrace, a young IT security company founded by the UK government’s cyber community — from GCHQ and other intelligence agencies — was started to do just that.
Headquartered in Cambridge, UK, Darktrace uses sophisticated mathematical models and Bayesian probability to detect anomalies, such as unusual transfers of corporate data in the wee hours of the morning, through its Darktrace Cyber Intelligence Platform (DCIP).
But in some cases, such data transfers may well be legitimate for travelling employees working remotely in a different time zone. The DCIP is smart enough to rule out such false alarms, by taking into account an individual’s usage patterns in its mathematical model.
Since its inception in 2013, Darktrace has detected a slew of anomalies – such as remote access attacks linked to malware, ransomeware infections and malicious web drive-by – in the networks of 75 companies around the world.
In one particular incident, Darktrace observed that a company machine was making anomalous connections to one IP address using Adobe Flash.
There was no evidence of the IP address being resolved through DNS, and the connections contained command names in HTTP GET requests. This incident appeared to be a covert method of communication that went undetected by firewalls.
Sanjay Aurora, general manager at Darktrace Asia Pacific, said the company is adept at identifying such unfamiliar threats – rather than known ones in rule-based security policies – by collecting user, device and network data. “It’s almost like a human immune system, where the body is able to determine what’s good or bad”.
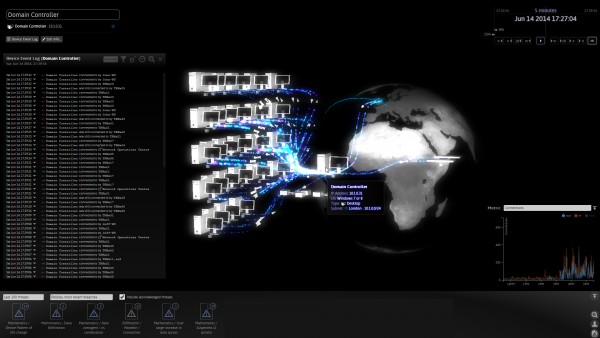
Darktrace customers will also get access to a 3-D visualisation tool that displays what is going on at any point in a corporate network, including data flows between devices, spikes in data transfers and a threat notification centre that shows a range of anomalies requiring investigation.
In March, the company announced that it has raised US$18 million from investors including Invoke Capital, Talis Capital, Hoxton Ventures and private individuals, valuing the company at US$80 million. It is in the midst of expanding its presence in Asia with new teams in Australia, Singapore and Japan.
DCIP is available as an appliance on a subscription basis. Aurora said the cost of the subscription would depend on the size of the network and the number of devices to be monitored.